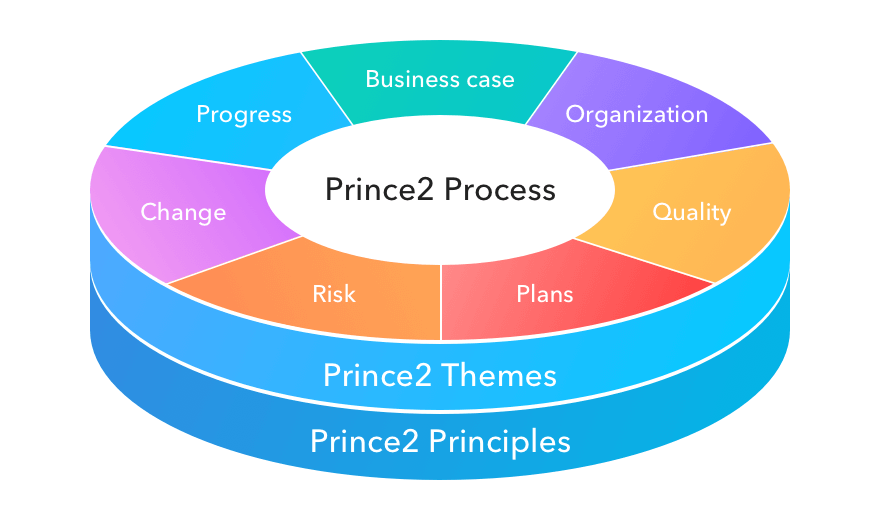
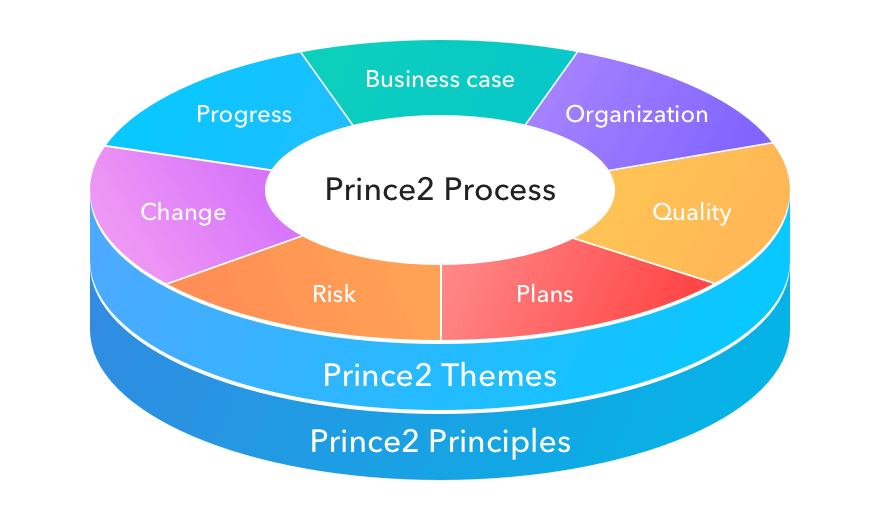
For many projects, there is a distinct lack of “team-building” activities. Team building activities are, of course, important in terms of ensuring success in difficult and novel environments. However, if project teams are formed without the proper skills and perspectives, the potential for fraud, liability and even lawsuits is huge.
So how are project teams formed?
Typically, a project manager will establish the function of the team and the team will then hire a primary producer for the specific area of the project. Primary producers are responsible for putting into place the project’s infrastructure, which will be important in order to deliver value and value to the business. As part of the hire, the primary producer’s team becomes the initial point of contact for the project, and that team will be in charge of day-to-day operations for the project.
Each project manager or primary producer will have a specific set of responsibilities, which will include:
Planning and conducting infrastructure development and sustainment activities (i.e. specifying the network and platforms that will be integrated into the project, defining the schema for the registries and managing the provisioning process).
Defining the general-purpose OR manager’s role, which will include oversight of the project’s overall mission and values, as well as the associated policies, procedures and standards.
Managing the organization’s business continuity, including through ongoing risk assessment and planning, as well as response and recovery.
Resourcing: identifying requirements, prioritizing them, and establishing limits and metrics for management.
These are just a few of the OR functions that must be performed by a Primary Recorder. As such, it is important to have a Primary Recorder for your organisation so that you can perform these important tasks and provide the best business continuity planning possible using PRINCE2 Training.
Design and deliver a Primary Infrastructure Management Application or Infrastructure project. This is the “brains” of the project, closely integrated within the overall business processes of the organisation and will form the basis of the organisation’s strategy for enabling value from an enterprise’s digital resources.
You perhaps have a number of businesses in your organisation that are keen to do this, particularly in the area of Security. You need to make sure that you have a robust and relevant policy in place that all teams within the organisation are aware of. Everyone must understand the importance of having a robust and externally audited policy in place.
Conduct an ASV audit of your organisation. Especially if your organisation is a small, close-knit group, it is important that you have a large number of security representatives throughout the organisation. Everyone must be encouraged to influence their team not just towards using security best practice, but also towards obtaining the right people to maintain the security.
Keep your team aware of the many benefits of Active Directory, particularly if your company is a small, local company with a number of remote employees. Also, make sure that they are aware of the changes to the organisation’s security procedures as they come through (e.g. Active Directory Services Changes). It is important that they are aware of not just how vulnerable their systems are, but also what the attackers could do if they had access to the system.
Ensure that the operation systems, gateways and servers are all upgraded to the latest versions. Security updates are released at a regular basis and will ensure that your system is always secure.
There are always new challenges and threats in the world of cyber security. The need for a robust Active Directory security service is essential and is based on establishing a relationship with your users and the administrators who control the resources. This means that you must engage with them, listen to their concerns and seek to understand why they need and will benefit from any changes that are made.
As one of the experts in the field of ethical hacking, I have seen many systems hacked in many ways. The attackers used “social engineering” techniques to breach the systems. This unfortunately is becoming more and more the preferred method of threat distribution. Employees may be more accepting of giving their passwords away if they personally know the person concerned or if they are afraid of them.
Fortunately, due to the rapid evolution of technology, we have a tool that allows us to secure the systems around us.